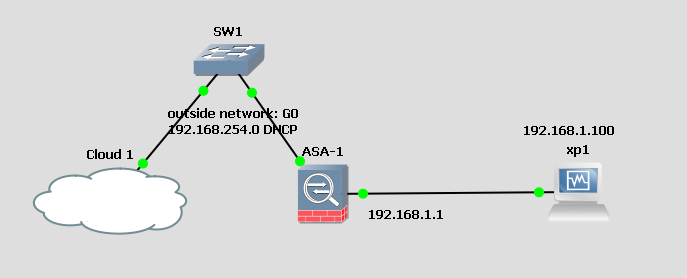
Using GNS3, the ASA 5520 has an ‘outside’ address of 192.168.254.247
The XP1 VM has been set up with Abbyss Web Server, running on Port 8080. You want all traffic from the 254 network to be able to reach the web server.
(Note, this is STATIC NAT, not DYNAMIC, because you have an individual host for the web service.
Step 1: Create a network object, and define its IP address:
ciscoasa(config)# object network outside-inside-web-server
ciscoasa(config-network-object)# host 192.168.1.100
Step 2 (still within network object) add your NAT statement
ciscoasa(config-network-object)# nat (inside, outside) static interface service tcp 8080 8080
Step 3: Define an access list allowing traffic from
ciscoasa(config-network-object)# access-list OutsideToWebServer permit tcp any host 192.168.1.100
(Note 1: the port is put in twice because it is source and destination port. You could translate the port here, but for a web server, source and destination port will be the same.)
(Note 2: The NAT statement and ACLis configured within the network object configuration)
Step 4: Apply the access list to the outside interface:
ciscoasa(config)# access-group OutsideToWebServer in interface outside
You should now be able to get to the web server anywhere on the ‘external’ network, which in this case, as it’s a lab, using GNS3, will still be your internal network.