Cisco 800 Series SOHO routers are intended for small branch offices. They are in effect two routers in one, with a separate IOS for WiFi.
Another issue they have in common is that they mostly have all switchports, so it is necessary to create VLANs and assign the ports as appropriate. One VLAN for the WAN, and one for the LAN.
There are 7 steps in a basic configuration:
- Configure inside and outside interfaces – IP addresses. Interfaces may be routed ports or SVIs, depending on the model of router.
- Create an access list which will form part of your NAT statement
- Create your NAT statement: ie ip nat inside source list (the access list you created) interface (the outside interface) overload.
- Add a default route: ip route 0.0.0.0 0.0.0.0 etc
- Create a DHCP server for inside addresses if desired.
- Set the LAN ports with BPDU Guard and portfast
- Set up SSH access to the router, along with a local user and pass.
Here is a sample setup using Packet Tracer, which has an 819 simulator:
———————————————————————————–
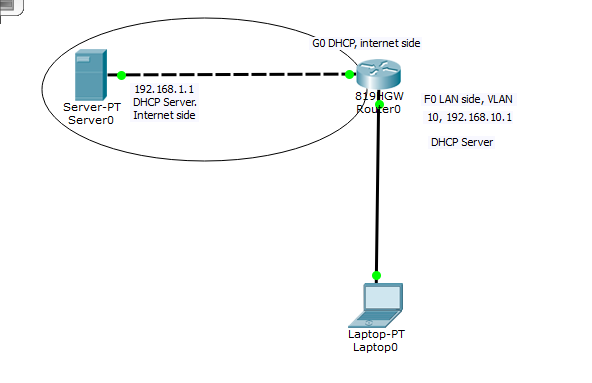
—————————————————————–
Step 1: Configure inside and outside interfaces:
Outside:
int g0
ip address dhcp
no shut
Inside:
Vlan 10
int vlan 10
IP address 192.168.10.1 255.255.255.0
No shut
Router(config)#int fa0
Router(config-if)#switchport mode access
Router(config-if)#switchport access vlan 10
Router(config-if)#no shut
Step 2: Create an access list which will form the basis of your NAT statement:
conf t
ip access-list extended NAT-ACL
permit ip 192.168.10.0 0.0.0.255 any
Step 3: NAT Statement
ip nat inside source list NAT-ACL interface G0 overload
I want to nat from the inside from the source ip range which is specified in my ACL and I want to NAT using the outside interface G0 and use overload so multiple addresses inside share.
Tell router which is inside and outside
int g0
ip nat outside
int VLAN 10
ip nat inside
Step 4. Default route: ip route 0.0.0.0 0.0.0.0 192.168.1.1
Step 5: Set up DHCP for the LAN
ip dhcp pool LAN1
network 192.198.10.0 255.255.255.0
default-router 192.168.10.1
DNS-server 8.8.8.8
lease 1 (number of days of the lease)
ip dhcp excluded-address 192.168.10.1 192.168.10.99
ip dhcp excluded-address 192.168.10.150 192.168.10.254
